Gimly’s Decentralized Identity Framework Is Built for Portability and Security
Gimly built a decentralized identify framework on EOSIO that offers users portability, security, and ease.

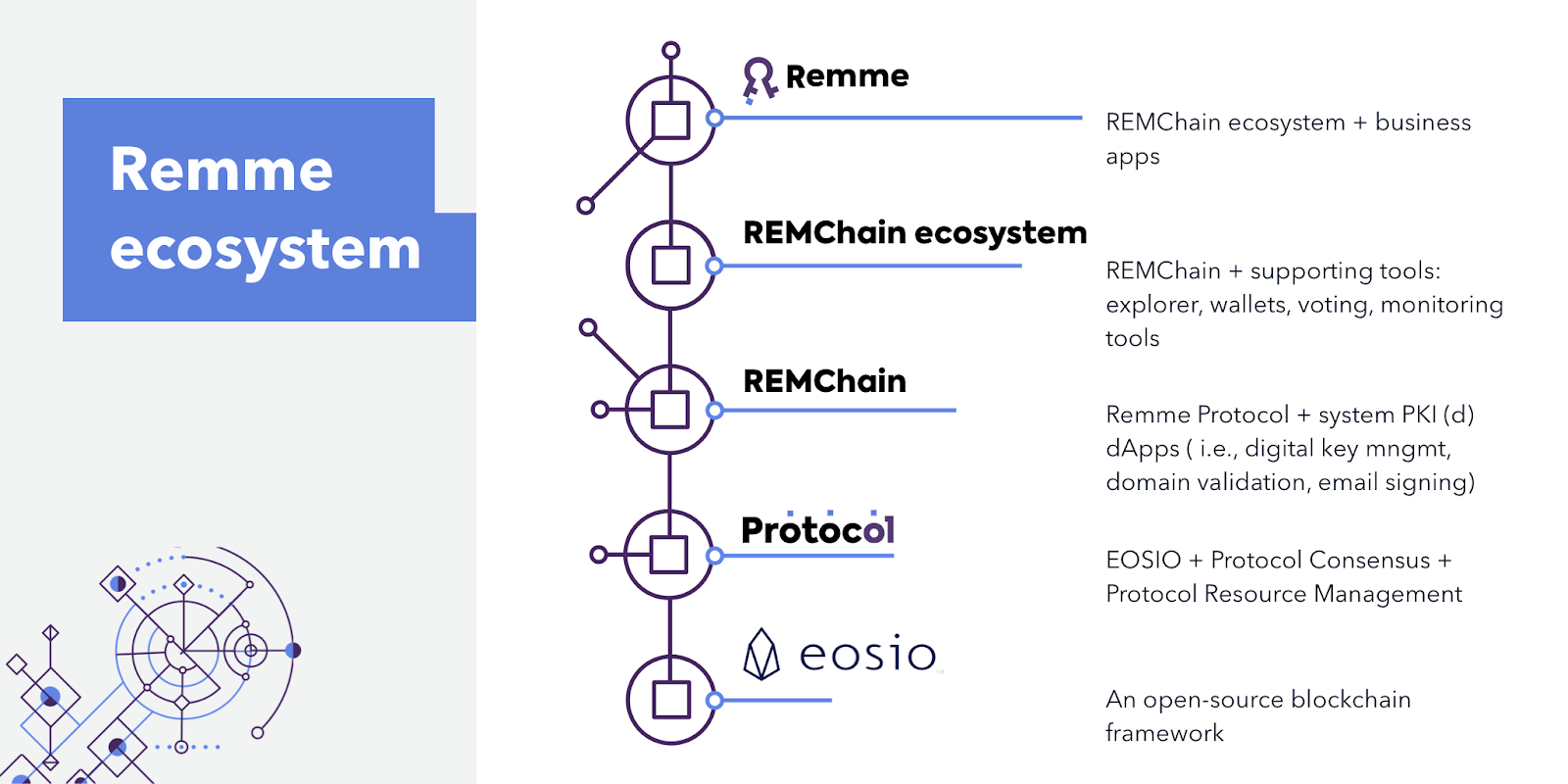
Remme is an ecosystem of identity and access management products with a digital key at its core. Developers can make use of Remme’s open source distributed PKI protocol, while their certificate management platform offers solutions for enterprise clientele. Remme was founded in 2015 with the goal of building a next-gen Public Key Infrastructure (PKI) protocol and suite of decentralized PKI-enabled apps to address the challenges of Web 3.0.
That PKI protocol utilizes the EOSIO™ codebase to create a decentralized system for storing and revoking digital keys in a highly secure manner.
Remme Protocol anchors the Remme ecosystem, including the blockchain layer to host identity information, tools on top of it that manage both machine and user identities, and finally the layer that enables custom apps for a variety of PKI use cases.
As an example, we have already implemented several pilots that utilize Remme Protocol, one of which is a blockchain-based customer authentication project for a Fortune 500 automotive manufacturer.
We are convinced that the PKI solution that was introduced in the 1970s is simply not capable of meeting the needs of the modern web, especially with such powerful new technologies emerging.
Today, just as 40 years ago, certificate authorities (CA) are responsible for digitally signing and publishing public key certificates using the CA’s key. This presents a single, centralized point of attack. Compromise the CA, and the entire suite of keys they oversee is in jeopardy.
The evolving needs of enterprises, their increased connectivity, and the enhanced capabilities of ever more sophisticated attackers have necessitated a transition to a more resilient alternative. That alternative resides on the blockchain, where many of the fundamental weaknesses of traditional PKI do not apply.
EOSIO forms an excellent base on which to develop Remme Protocol. However, we made the decision to launch as an independent network because we wanted to be able to customize key components, such as configuring the consensus so that Block Producers themselves could serve as the network’s long-term stakeholders.
We also wanted to simplify the resource economy by managing RAM, NET, and CPU simultaneously, powered by the REM token, so as to improve UX and eliminate much of the complexity from the perspective of end-users. Using our own fork of EOSIO also enables us to create bespoke PKI-related features out of the system smart contracts.
We began by customizing the EOSIO codebase to accommodate our specific use cases and token economy. Since we have a large community of token holders and Block Producers, we had to explain to them the changes in detail. We detailed these changes in a series of educational blog posts and visualized the key modifications related to the features we inherited from EOSIO, namely its consensus, governance and resource economy.
We actually started out using Hyperledger Sawtooth as our blockchain framework but encountered an array of problems that persisted throughout testing. As the date of the first testnet drew nearer, it was evident that Sawtooth wasn’t cut out to handle the sort of use cases we’d envisaged, and certainly not at scale.
It was evident that we needed an alternative blockchain solution that was more flexible, customizable and capable of operating at scale to serve millions of connected devices. After exploring the alternatives, it became apparent that EOSIO was by far the best option for Remme.
The main factors that influenced our decision were DPOS consensus, and that the EOSIO resource management concept fit very well into our token economy, and the decentralized PKI concept.
EOSIO has been extensively tested at a very high level and has significant industry recognition. It works on a global scale, supporting hundreds of commercial-scale dApps. Additionally, the EOSIO ecosystem has a tremendous developer community that expands the codebase and the independent surrounding tools towards every possible use case. The protocol’s ability to support commercial-scale dApps that are suitable for enterprises sealed it.
Many of the characteristics for which blockchain technology is renowned are naturally suited to identity and access management. These include built-in transparency, censorship resistance, and widespread availability via a distributed network of nodes.
Blockchain based systems also eliminate certain attack vectors including man in the middle (MITM) attacks. Because enterprises are interacting directly with the blockchain, without reliance on a central authority, stealing or compromising certificates becomes exponentially harder.
Moreover, because the blockchain itself is supported by a broad array of entities, and overseen by a global system of validator nodes, businesses can rest assured that services will be maintained in perpetuity, without the risk of the Certificate Authority going out of business or cutting them off.
Passwordless user authentication and smart device authentication are two of the most obvious applications, but the number of use cases is limitless; we intend to focus on introducing identity solutions at first such as digital key management, domain validation, and SSH key management. In the future, we envision Remme Protocol being used to control access for thousands of businesses, hundreds of thousands of users, and millions of IoT devices.
Remme’s core team has a wealth of blockchain and cybersecurity experience that stretches back almost a decade.
Our, CTO Roman Cherednik, has extensive experience in blockchain and PKI project development, including a global software development company with $650M revenue with over 13,000 employees, as well as a stint at an established crypto exchange.
Then there’s our Head of Business Development Sid Desai, who leads our US office. Thanks to a career at Certificate Authority GlobalSign, he’s been deeply involved with PKI and has seen the many ways in which it can be improved.
With 30 additional seasoned tech and marketing experts, Remme is well placed to make good on its promise of spearheading the creation of next-gen PKI solutions.

For us, it is imperative that Remme Protocol is fully open source.
This is expected of blockchain technology, the value proposition of which hinges partially upon a fully transparent and open framework, and without which mass trust and thus mass adoption would be impossible.
The benefits of harnessing open source technology include being able to leverage advanced software such as EOSIO, which saves us from having to build everything from scratch and provides certain security and developmental assurances.
In return, we hope that the open source applications we build upon EOSIO will be utilized and expanded upon by other developers. We have a very strong open source Remme community, including third-party devs who are solving an array of real-world challenges using our tech.
We have huge plans in the pipeline! At Remme, we believe that the way the modern world handles digital identities doesn’t cut it anymore. The number of digital identities, both human and machine, continues to grow at an incredible pace. That’s why we’re determined to lead the transition towards secure and simplified identity management.
In terms of Remme Protocol, we plan to launch the mainnet by the end of this year. In 2020, we’ll focus on addressing other next-gen PKI challenges such as decentralized domain validation and SSL/TLS, email security, code signing and browser integrations. And 2021 will be dedicated to the IoT universe.
As for product development, we intend to further develop Remme Auth, which addresses human identity management, and we are actively developing our second flagship product, Keyhub, which is for machine identity management.
Unlike Auth, which will begin its journey together with Remme Protocol from mainnet launch, Keyhub is already live and already solves the problems of today’s PKI world related to certificate lifecycle management. More than 100 enterprises are using Keyhub already.

Once we’ve finished tailoring the consensus and resource management layer, we intend to focus on developing system smart contracts to add account attribute management. This will enable attribute-based credentials and access control use cases. Then we will work on external state verification. This will facilitate consolidated on-chain resolutions about events that reside and occur outside the blockchain. As a result, on-chain smart contracts and the applications built on Remme Protocol can subscribe and react to the events that happen in the real world.
After these two components, we will continue to deliver extra PKI-related features out of the system smart contracts required for other use cases such as email security and code signing.
Our #BuiltOnEOSIO series showcases some of the amazing projects leveraging EOSIO technology to build a more secure and connected world. If you would like to suggest a project for us to feature please send an email to [email protected] for our Developer Relations team to review.
– Block.one Developer Relations team
. . .
Important Note: All material is provided subject to this important notice and you must familiarize yourself with its terms. The notice contains important information, limitations and restrictions relating to our software, publications, trademarks, third-party resources and forward-looking statements. By accessing any of our material, you accept and agree to the terms of the notice.