EOSIO Tools Release: WebAuthn Example App Update

With the stable release of EOSIO 2 introducing support for WebAuthn, application developers can begin integrating support for YubiKeys and other WebAuthn enabled 2FA devices in their applications. Today we are excited to announce a WebAuthn Example Application update that provides a walkthrough for developers interested in integrating WebAuthn in their projects to use a device like a YubiKey for two-factor authentication (2FA) when signing transactions.
WebAuthn allows for the use of hardware devices, like YubiKeys, for secure 2FA in a browser without extensions or other software installed on your device. We are excited to see EOSIO developers build support for WebAuthn 2FA in EOSIO applications, developed by notable technology companies who are part of the World Wide Web Consortium (W3C).
Support for WebAuthn in EOSIO is a step towards more secure and seamless authentication in blockchain applications. We encourage application developers to join the first wave of early adopters testing the applications of this technology for blockchain platforms and we will continue to investigate mechanisms to support startup and enterprise grade applications of this innovative technology.
The Problem with Passwords
Relying solely on password based credentials isn’t always enough. Malicious actors use numerous methods to trick unsuspecting users by way of phishing attempts, physical security breaches, corrupt websites or embedded links, or even messages impersonating a friend or coworker that are sent in an effort to trick someone to click on a bad link. When criminals are successful, servers can be breached and passwords exposed.
WebAuthn 2FA introduces a more robust security layer for high-risk transactions, augmenting existing best practices in blockchain applications. WebAuthn enabled devices, like a YubiKey, can be registered with each application a user wants to authenticate with. The public key is only shared with that specific application and the private key remains enclaved in the YubiKey. Once registered, a user can provide 2FA verification for blockchain transactions with just a tap using their YubiKey. When enabled as a 2FA layer, WebAuthn devices can diminish illicit account access.
By managing 2FA authentication credentials entirely within hardware devices, WebAuthn has been shown to essentially mitigate entire classes of attacks such as phishing. Users remain protected because, without the hardware device to verify, criminals who normally rely on stolen passwords can’t bypass 2FA roadblocks.
How It Works
We have released an updated WebAuthn Example Application for reference that describes how developers can integrate a WebAuthn based 2FA layer for users signing transactions considered high-risk. Developers should note that in order to successfully use a 2FA device like a YubiKey with the WebAuthn Example Application, they will need to reference the EOSJS V21.0.0 Release Candidate until a stable release is available.
In the example app, a user logs in to a property rental application called Tropical. In the application there are two types of possible transactions: low-risk transactions “liking” properties, and high-risk transactions “renting” properties. The user follows the steps to designate a YubiKey as their 2FA method for high-risk “renting” property transactions.
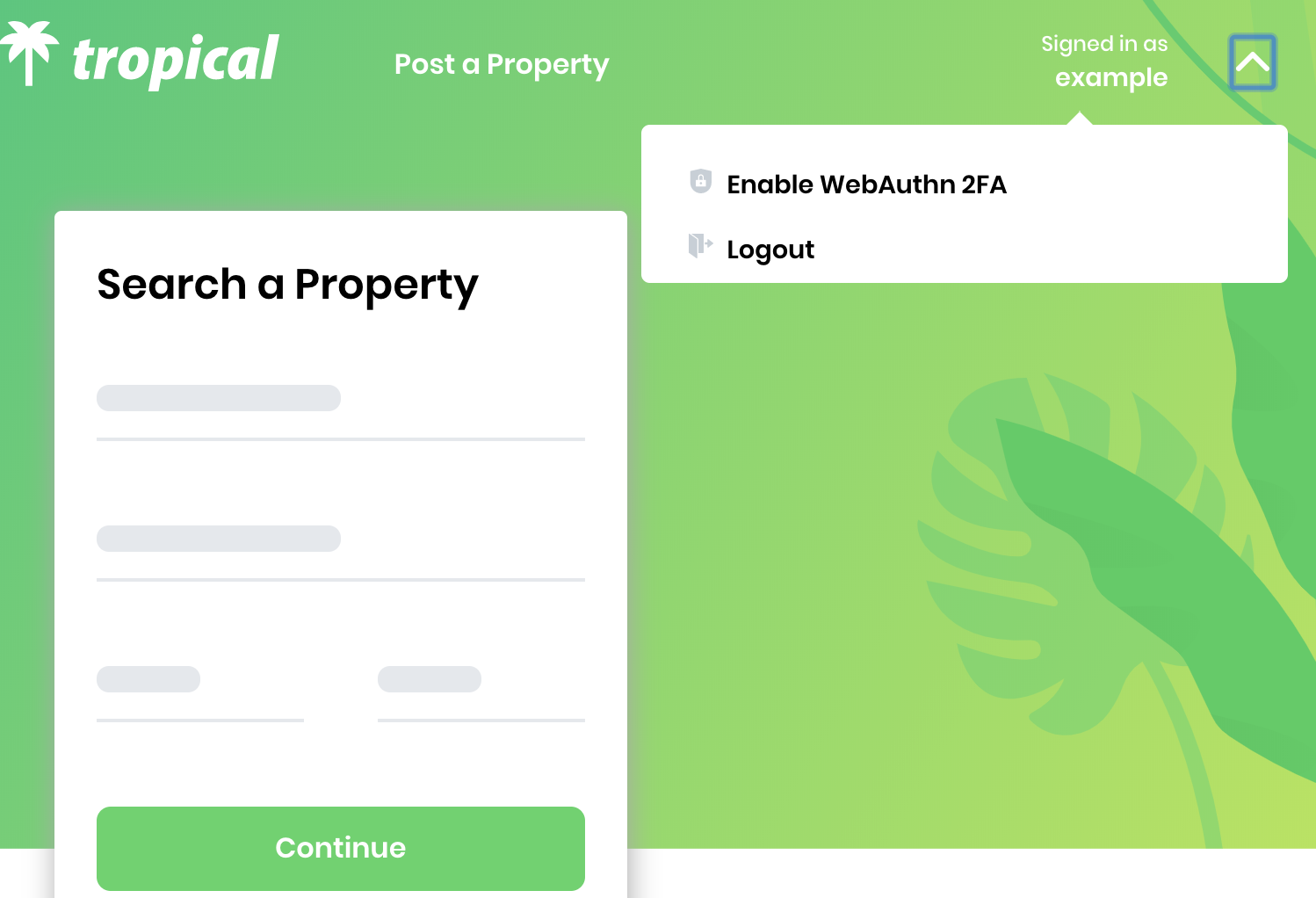
First the user logs in. Next they select “Enable WebAuthn 2FA” from a dropdown menu. A WebAuthn 2FA pairing works with either a built in sensor, such as a TouchID reader on a Macbook Pro, or with a USB Key, such as a YubiKey. Users make their selection and activate their selected device by either applying their fingerprint to the TouchID sensor, inserting their YubiKey into the device, or placing their YubiKey within range of the device’s NFC sensor. After a final verification, their 2FA method of choice is registered.
When a user performs a high-risk activity that requires 2FA, the client requests a challenge from the server. In response, the server returns the challenge, signed with its own private key generated from the user’s public key and concrete data correlated with the high-risk activity, in this case, renting a property. After the client receives the server’s response the client makes a new request, this time for the user verify by way of 2FA. Once verified, the challenge is wrapped as a provably authenticated transaction which is then broadcast to the chain.
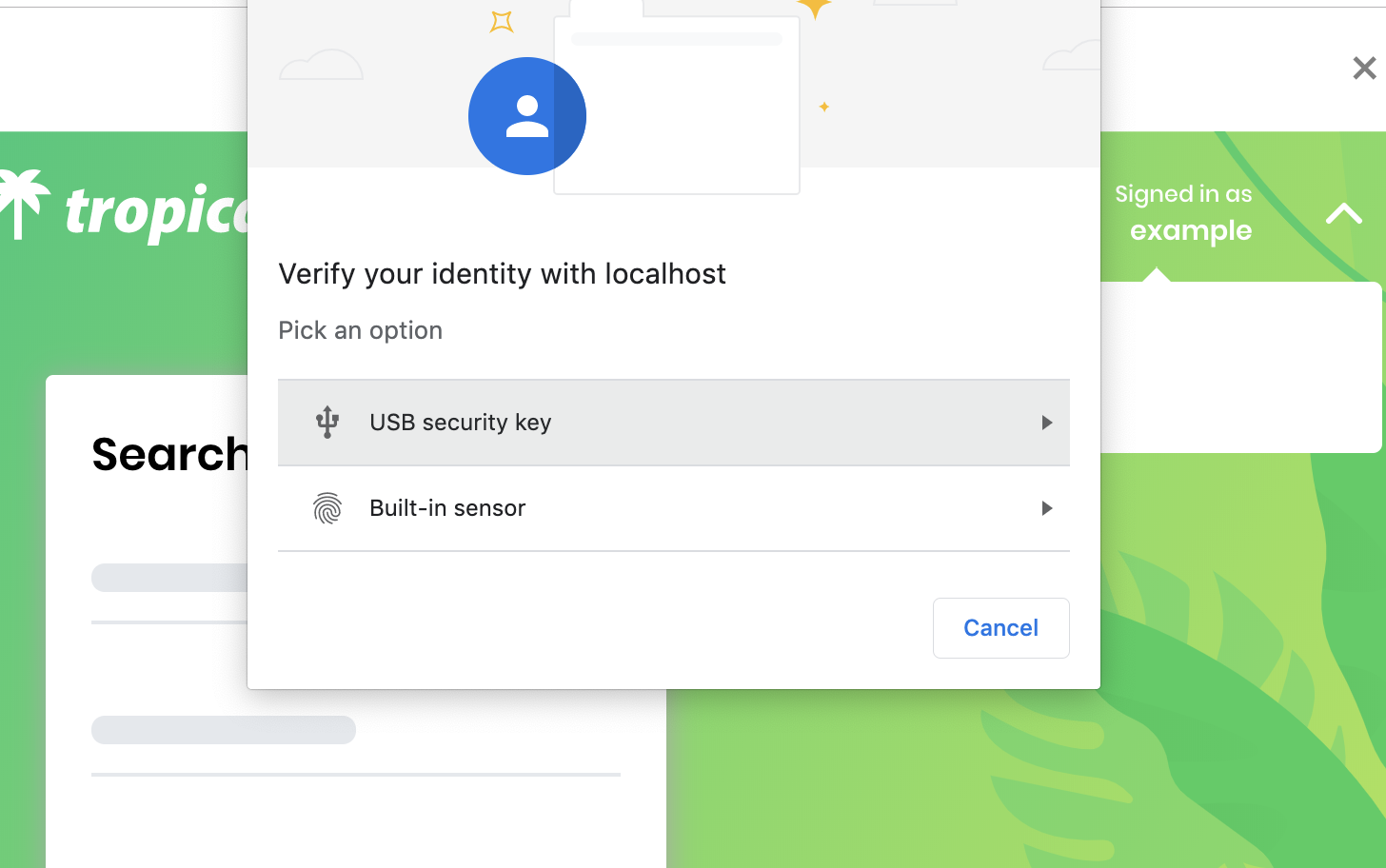
Developers can refer to the WebAuthn Example Application release notes for an in-depth walkthrough of steps to follow to enable WebAuthn based 2FA and provide users additional security for high-risk transactions.
Community Developer Feedback
This example application is built to show how to support WebAuthn in an EOSIO Application, but we are excited to see how the developer community tests and adopts this functionality in production environments. We are currently seeking feedback from developers who integrate WebAuthn in their EOSIO applications to help us understand additional use cases where this technology may be beneficial in EOSIO applications.
EOSIO branded YubiKeys will soon be available for developers to start integrating support for WebAuthn for in EOSIO applications. Join first movers and help create a safe and secure ecosystem by building 2FA support in your application today.
Stay Connected
We’re committed to bringing innovative solutions, such as WebAuthn 2FA, to the EOSIO ecosystem. If you would like to offer feedback and work more closely with our team to improve EOSIO for developers, you can send our developer relations team an email at [email protected].
. . .
Important Note: All material is provided subject to this important notice and you must familiarize yourself with its terms. The notice contains important information, limitations and restrictions relating to our software, publications, trademarks, third-party resources and forward-looking statements. By accessing any of our material, you accept and agree to the terms of the notice.